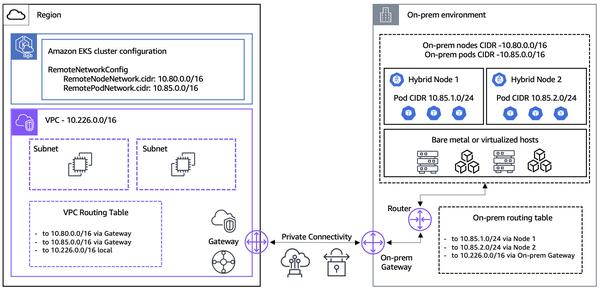
Mandiant, a leading cybersecurity firm, has published a report highlighting the alarming patterns of heists in the Web3 world. The report provides an in-depth analysis of various methods employed by attackers, including social engineering, smart contract exploits, and vulnerabilities in exchange platforms. One particularly interesting aspect is the focus on social engineering attacks targeting developers and finance personnel in Web3 organizations. The report illustrates how attackers utilize fake job offers to infiltrate systems and steal credentials. Their use of malware such as COVERTCATCH and RUSTBUCKET is documented in detail, highlighting the evolving threat landscape facing the Web3 industry. Furthermore, the report delves into the exploitation of smart contracts, focusing on reentrancy and flash loan attacks. It provides a comprehensive analysis of high-profile cases like the Curve Finance and Euler Finance hacks, explaining the mechanisms and impact of these attacks. What I found particularly intriguing is how the report unveils vulnerabilities in smart contract code and how attackers can exploit them to steal funds. The report also provides an insightful analysis of governance attacks, focusing on the Tornado Cash case. It demonstrates how attackers can manipulate decentralized voting systems to gain control of projects and plunder their funds. The emphasis on the social engineering employed to trick community members into voting for malicious proposals highlights the importance of security awareness and proposal validation within the Web3 community. Overall, Mandiant's report offers a valuable analysis of the evolving landscape of heists in Web3. It underscores the need for robust security measures, including strong anti-social engineering measures, secure smart contract development practices, and resilient governance mechanisms. By understanding the methods and tactics employed by attackers, individuals and organizations in the Web3 space can better strengthen their defenses and protect themselves from potential threats.
DeFied Expectations — Examining Web3 Heists
Google Cloud