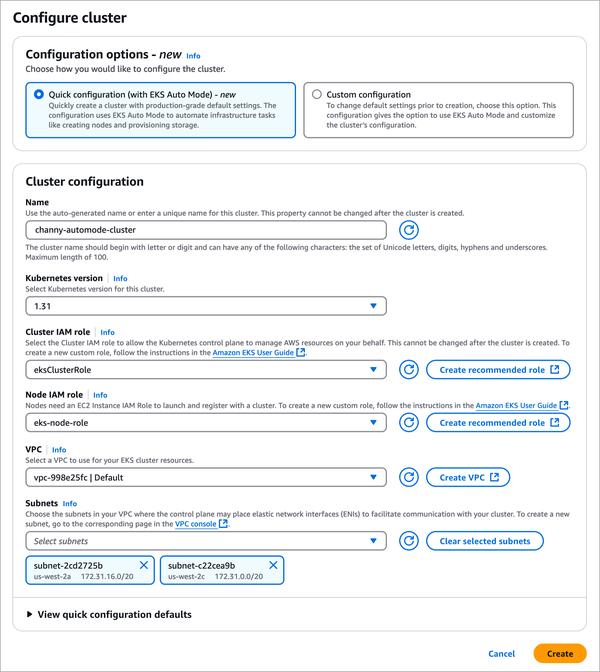
Nino Isakovic and Chuong Dong published a blog post titled "LummaC2: Obfuscation Through Indirect Control Flow." This blog post delves into analyzing a control flow obfuscation technique employed by recent LummaC2 (LUMMAC.V2) stealer samples. In addition to the traditional control flow flattening technique used in older versions, the malware now leverages customized control flow indirection to manipulate the malware's execution. This technique thwarts all binary analysis tools, including IDA Pro and Ghidra, significantly hindering the reverse engineering process and automation tooling designed to capture execution artifacts and generate detections. To provide insights to Google and Mandiant security teams, the authors developed an automated method for removing this protection layer through symbolic backward slicing. By leveraging the recovered control flow, they can rebuild and deobfuscate the samples into a format readily consumable for any static binary analysis platform. I found the use of symbolic backward slicing to remove this protection layer particularly interesting. This approach can be quite effective in mitigating the effectiveness of control flow obfuscation techniques. I believe this research will be highly valuable to malware analysts looking to enhance their reverse engineering capabilities.
LummaC2: Obfuscation Through Indirect Control Flow
Google Cloud