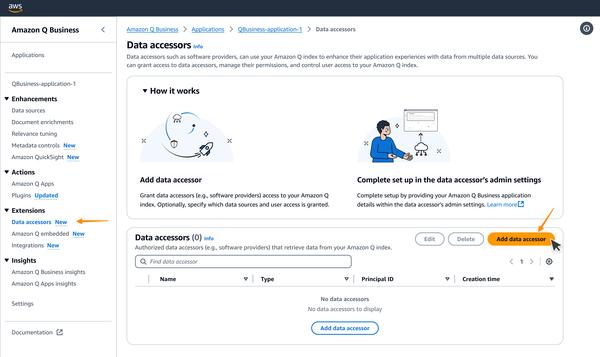
AWS has updated CloudTrail Lake, providing new capabilities to enhance cloud visibility and investigations. These updates include enhanced filtering options for CloudTrail events, cross-account sharing of event data stores, general availability of generative AI-powered natural language query generation, AI-powered query results summarization capability (in preview), and comprehensive dashboard capabilities, including a high-level overview dashboard with AI-powered insights (in preview), a suite of 14 pre-built dashboards for various use cases, and the ability to create custom dashboards with scheduled refreshes.
I was particularly impressed by the enhanced filtering options. By providing more granular control over AWS activity data, organizations can improve the efficiency and precision of security, compliance, and operational investigations. Additionally, the new filtering options help reduce analysis workflow costs by ingesting only the most relevant event data into CloudTrail Lake event data stores.
Cross-account sharing of event data stores is another valuable feature. By enabling secure sharing of event data stores with selected AWS principals through Resource-Based Policies (RBP), organizations can enhance collaborative analysis within organizations. This functionality allows authorized entities to query shared event data stores within the same AWS Region where they were created.
Overall, the new features in AWS CloudTrail Lake represent a major advancement in providing a comprehensive auditing, logging, and analysis solution. These enhancements provide the ability to gain deeper understanding and conduct investigations more rapidly, assisting with more preventative monitoring and faster incident handling across your entire AWS environments.